Navigating the Cyber Battlefield: Unraveling the Top Types of Cyber Attacks

Introduction:
The rise of technology has ushered in unprecedented opportunities but has also paved the way for various cyber threats. As businesses and individuals continue to rely on digital platforms for communication, commerce, and information sharing, the importance of understanding and safeguarding against cyber attacks cannot be overstated. In this blog post, we will delve into the top types of cyber attacks, shedding light on the methods employed by malicious actors to compromise digital security.
Phishing Attacks:
Phishing attacks are one of the most common and deceptive cyber threats. In a phishing attack, cybercriminals disguise themselves as trustworthy entities to trick individuals into revealing sensitive information, such as passwords or credit card details. These attacks often involve convincing emails, messages, or websites that mimic legitimate sources, exploiting human psychology to manipulate victims into taking actions that compromise their security.
Ransomware:
Ransomware has gained notoriety in recent years for its ability to cripple entire systems. This type of attack involves encrypting a victim's files or systems, rendering them inaccessible. The attacker then demands a ransom, usually in cryptocurrency, in exchange for providing the decryption key. Ransomware attacks can have severe consequences, ranging from financial losses to significant operational disruptions.
Denial of Service (DoS) Attacks:
Denial of Service attacks aim to overwhelm a system, network, or website with an influx of traffic, rendering it inaccessible to legitimate users. Distributed Denial of Service (DDoS) attacks, a more sophisticated variant, involve multiple compromised systems working in concert to flood the target. The objective is to exhaust resources and disrupt normal functioning, causing downtime and potential financial losses for the targeted organisation.
Man-in-the-Middle (MitM) Attacks:
In a Man-in-the-Middle attack, an intruder intercepts and potentially alters communication between two parties without their knowledge. This type of attack can occur in various forms, such as eavesdropping on Wi-Fi networks or intercepting communication between a user and a website. The attacker can then gain access to sensitive information, including login credentials and personal data.
SQL Injection:
SQL injection attacks target databases by manipulating input fields to execute malicious SQL commands. If a web application fails to validate user input adequately, attackers can insert harmful SQL statements, potentially gaining unauthorised access to databases or even causing data loss. Proper input validation and parameterised queries are crucial for preventing SQL injection vulnerabilities.
Cross-Site Scripting (XSS):
Cross-Site Scripting attacks involve injecting malicious scripts into web pages viewed by other users. By exploiting vulnerabilities in web applications, attackers can execute scripts within the context of a user's browser, potentially stealing sensitive information or session cookies. Web developers must implement secure coding practices and input validation to mitigate the risk of XSS attacks.
Zero-Day Exploits:
Zero-day exploits target vulnerabilities in software or hardware that are unknown to the vendor. Cybercriminals leverage these undiscovered weaknesses to launch attacks before a fix or patch is available. Organisations must stay vigilant, implementing robust security measures and keeping software up-to-date to minimise the risk of falling victim to zero-day exploits.
DNS Spoofing:
DNS Spoofing involves manipulating the Domain Name System (DNS) to redirect users to malicious websites. By compromising DNS servers or injecting false information, attackers can trick users into unknowingly interacting with fraudulent sites, potentially leading to phishing attacks or the installation of malware.
Conclusion:
As our reliance on digital platforms continues to grow, so does the importance of understanding and safeguarding against cyber threats. By familiarising ourselves with the various types of cyber attacks, individuals and organisations can take proactive measures to bolster their digital defences. Through a combination of cybersecurity awareness, robust policies, and the implementation of cutting-edge technologies, we can navigate the cyber battlefield with resilience and security.
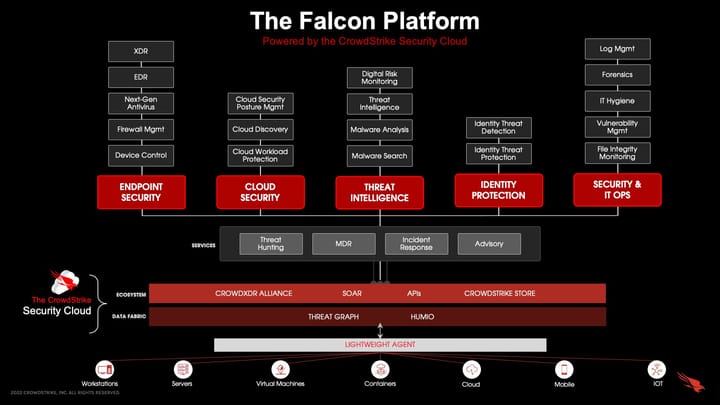

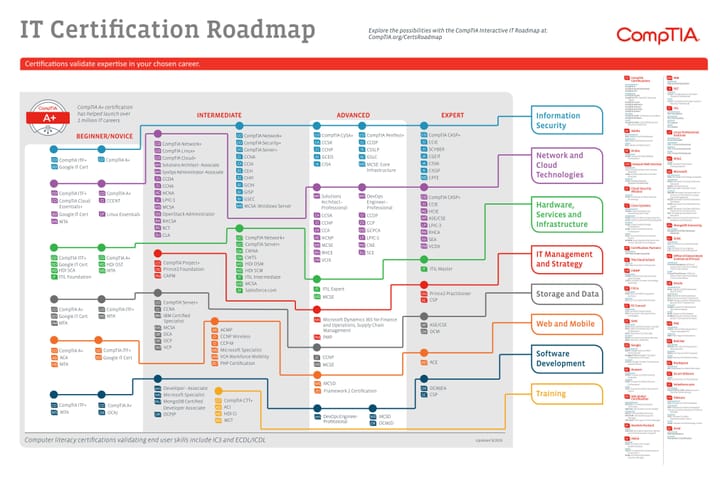
Comments ()